고정 헤더 영역
상세 컨텐츠
본문
- Python Aes Library
- Python Cryptography Generate Aes Keyboard
- Python Cryptography Generate Aes Key Bank
- Python Crypto Generate Aes Key
This is an exercise in secure symmetric-key encryption, implemented in purePython (only built-in libraries used), expanded from Bo Zhu's (http://about.bozhu.me)AES-128 implementation at https://github.com/bozhu/AES-Python

- AES-128, AES-192 and AES-256 implementations in pure python (very slow, butworks).Results have been tested against the NIST standard (http://csrc.nist.gov/publications/fips/fips197/fips-197.pdf)
- CBC mode for AES with PKCS#7 padding (now also PCBC, CFB, OFB and CTR thanks to @righthandabacus!)
encryptanddecryptfunctions for protecting arbitrary data with apassword
Python Aes Library
Note: this implementation is not resistant to side channel attacks.
Generation - python generate aes key Encrypt & Decrypt using PyCrypto AES 256 (6) Another take on this (heavily derived from solutions above) but. Aug 10, 2018 This tutorial explains how to encrypt and decrypt text using private and public key encryption, also known as asymmetric encryption. AES cryptography implementation with Python Complete.
Although this is an exercise, the encrypt and decrypt functions shouldprovide reasonable security to encrypted messages. It ensures the data iskept secret (using AES), blocks are encrypted together (CBC), the samemessage encrypted twice will have different ciphertexts (salt), the ciphertexthasn't been tampered with (HMAC) and the key has some defense against brute-force(PBKDF2).
The algorithm is as follows:

-
16 random bytes of salt are extracted from the system's secure random numbergenerator (usually /dev/urandom)>
-
The given master key is stretched and expanded by PKBDF2-HMAC(SHA256) usingthe salt from 1), to generate the AES key, HMAC key and IV (initializationvector for CBC).
-
The given message is encrypted with AES-128 using the AES key and IV fromstep 2), in CBC mode and PKCS#7 padding.
-
A HMAC-SHA256 is generated from the concatenation of the salt from 1) andthe ciphertext from 3).
-
The final ciphertext is HMAC + salt + ciphertext.
Python Cryptography Generate Aes Keyboard
Security overview:
Python Cryptography Generate Aes Key Bank
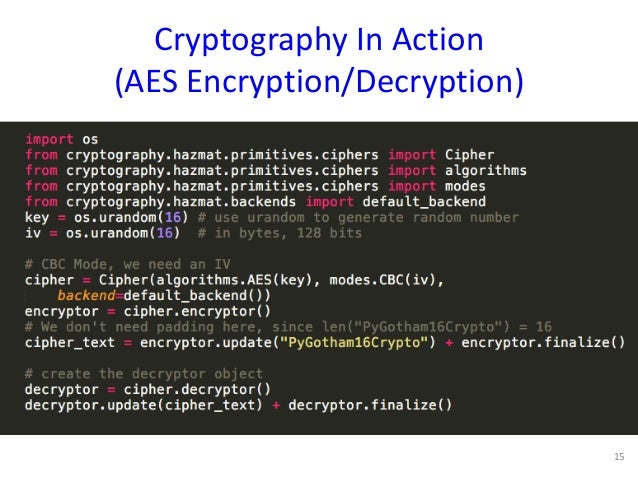
Python Crypto Generate Aes Key
-
The random salt ensures the same message will map to different ciphertexts.
-
The HMAC ensures the integrity of both the entire ciphertext and the PKBDF2salt; encrypt-then-mac prevents attacks like Padding Oracle.
-
Bytes from keys, iv and salt are not reused in different algorithms.
-
PBKDF2 key stretching allows for relatively weak passwords to be used as AESkeys and be moderately resistant to brute-force, but sacrificing performance.




